- Print
- PDF
This page describes how access to Autoform DM systems and their applications is controlled, and describes how IdP group memberships (via Keycloak) can control this access.
It also describes two distinct security models (group-mapped access and role-mapped access) for managing how Autoform DM role assignments are made in an SSO environment. The model that you choose depends on whether you want to minimize the complexity of the IdP configuration, or whether you want to maximize centralization of control into the IdP.
Autoform DM Security Management
In Autoform DM, roles control whether a user has admin-level access or user-level access to an Autoform DM system. Autoform DM groups can control a user’s access to import and search applications.
Roles
A user’s role assignment (or lack of) determines whether that user can access the Autoform DM application itself. It also determines the capacity (user or admin) that they can access it in.
In both SSO security models, the membership of security groups in the IdP determines the role assignments of Autoform DM users. Security groups in the IdP are described later in this page.
Groups
Autoform DM groups can control access to the search and import applications that Autoform DM is configured to provide.
To gain access to a particular application, a user can be made a member of the relevant Autoform DM group. Even if their role grants them “user-level access” to an Autoform DM instance, the user must still be a member of the groups that will grant them access to the import and search applications that they need to use.
Autoform DM Group Membership and Role Assignment in an SSO Environment
Standard SSO protocols including Open ID Connect (OIDC) transfer user identity, role, and group information from the IdP to Keycloak, and from Keycloak to Autoform DM. These flows enable IdP groups and roles to be mapped to Keycloak groups and roles, and enable those Keycloak groups and roles to be mapped to Autoform DM groups and roles. In this way, IdP group and role memberships control Autoform DM group memberships and role assignments via Keycloak.
Roles can be assigned to users at the Keycloak level (group-mapped access) or the IdP level (role-mapped access).
Group-Based Access Inheritance
Formpipe recommends that, in the IdP, the groups that control Autoform DM application access are members of groups that control Autoform DM role assignments. This enables a powerful inheritance of access.
For example, if the group that represents employees who process invoices (for example, invoice-team) is itself a member of the group that controls user-level access to the main production Autoform DM system (for example, prod-users), then assigning a user membership of invoice-team will automatically give them membership of the prod-users group. Both memberships together will ultimately grant them the ability to:
Access Autoform DM as a non-administrative user.
Access any applications that Autoform DM is configured to provide “invoice team” members access to.
Security Models for Role Assignment
A user’s membership of the Autoform DM groups that control application access is managed through their membership of specific IdP and Keycloak groups (known as application groups due to their purpose). As described above, IdP groups map to Keycloak groups, and Keycloak groups can map to Autoform DM groups.
However, there are two distinct ways to manage how IdP group memberships drive Autoform DM role assignments. Both of these methods result in the user being assigned role memberships in Keycloak (and consequently Autoform DM), but differ in where the groups (that manage who is assigned each role) are mapped to roles:
Group-mapped access: Groups are mapped to roles in Keycloak.
Role-mapped access: Groups are mapped to roles in the IdP.
From this point, this guide refers to these groups in the IdP and Keycloak as security groups. In general, the recommended approach is to create security groups for each environment and access level grouping. For example: dev-admins, dev-users, uat-admins, uat-users, prod-admins, and prod-users.
Each of the two security models introduced above has advantages and disadvantages.
The method that you choose will depend on your objectives. For example, role-mapped access enables greater centralization of control (over the security configuration) because role assignments are made in the IdP, but at the cost of additional complexity of configuration because app roles and role assignments must be created and managed outside of Keycloak.
Formpipe recommends group-mapped access unless there is a strong need for an alternative approach.
Group-Mapped Access
In summary:
In the IdP, users are assigned to security groups.
These groups are mapped to Keycloak security groups.
Keycloak security groups are assigned Keycloak roles.
Keycloak role assignments determine Autoform DM role assignments.
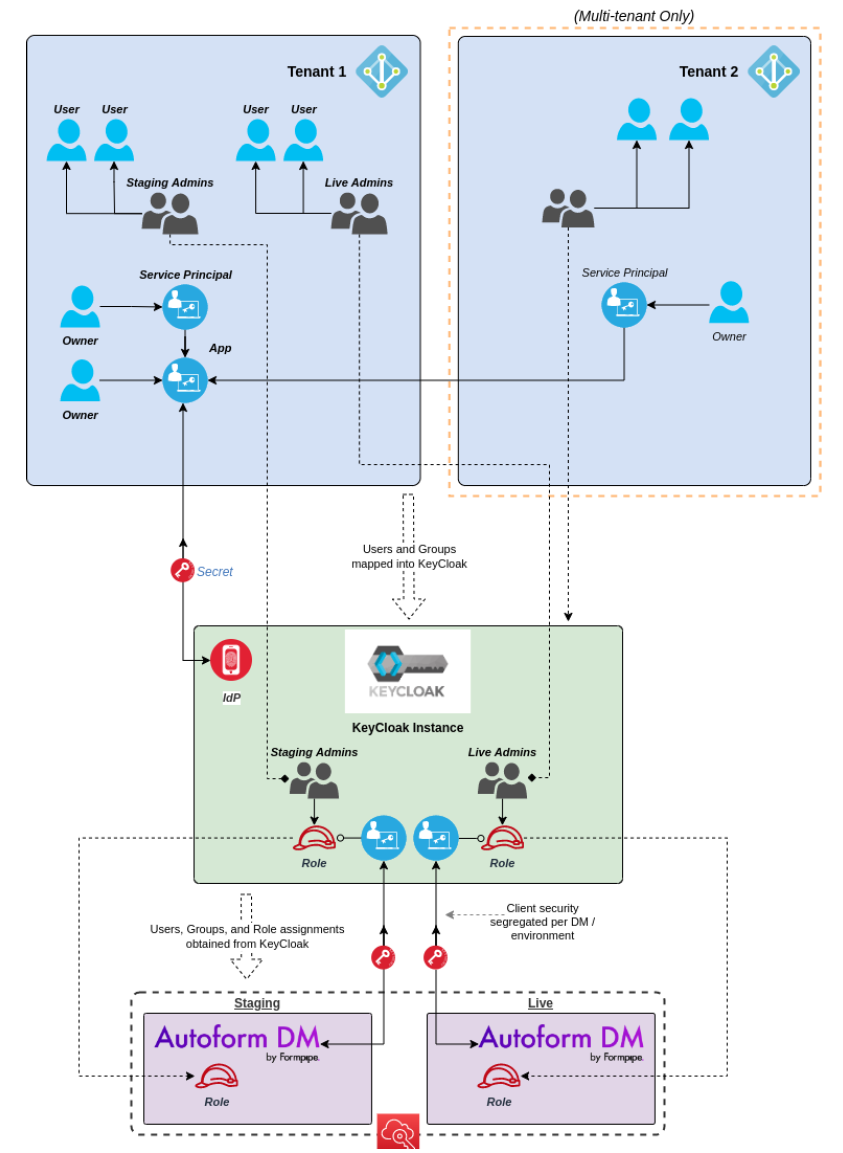
In this approach to security:
IdP security groups representing role groupings are created for each Autoform DM environment. For example: Staging Users, Staging Admins, Live Users, and Live Admins.
No app roles are defined.
Keycloak security groups that correspond to the IdP groups are created.
Keycloak roles that correspond to Autoform DM instance-specific roles are created.
Each of the Keycloak security groups is assigned to a corresponding Keycloak role.
When Autoform DM receives the information from Keycloak about a user’s role, it assigns the corresponding Autoform DM role to the user.
The advantage of this approach is that it reduces some of the configuration complexity outside Keycloak, because no app roles need to be created or assigned. The disadvantage is that it moves management of role assignment purely to KeyCloak, so this approach is less suitable when a major objective is to centralize access management.
Formpipe recommends using group-mapped security unless there is a strong need to use an alternative.
Role-Mapped Access
In summary:
In the IdP, users are assigned to security groups.
IdP security groups are assigned to app roles. These roles are mapped to Keycloak roles.
Keycloak role assignment determines Autoform DM role assignment.
Essentially, app roles are created in the IdP to match those that are available in Autoform DM. These IdP app roles are mapped to Keycloak roles, and those Keycloak roles are mapped to Autoform DM instance-specific roles.
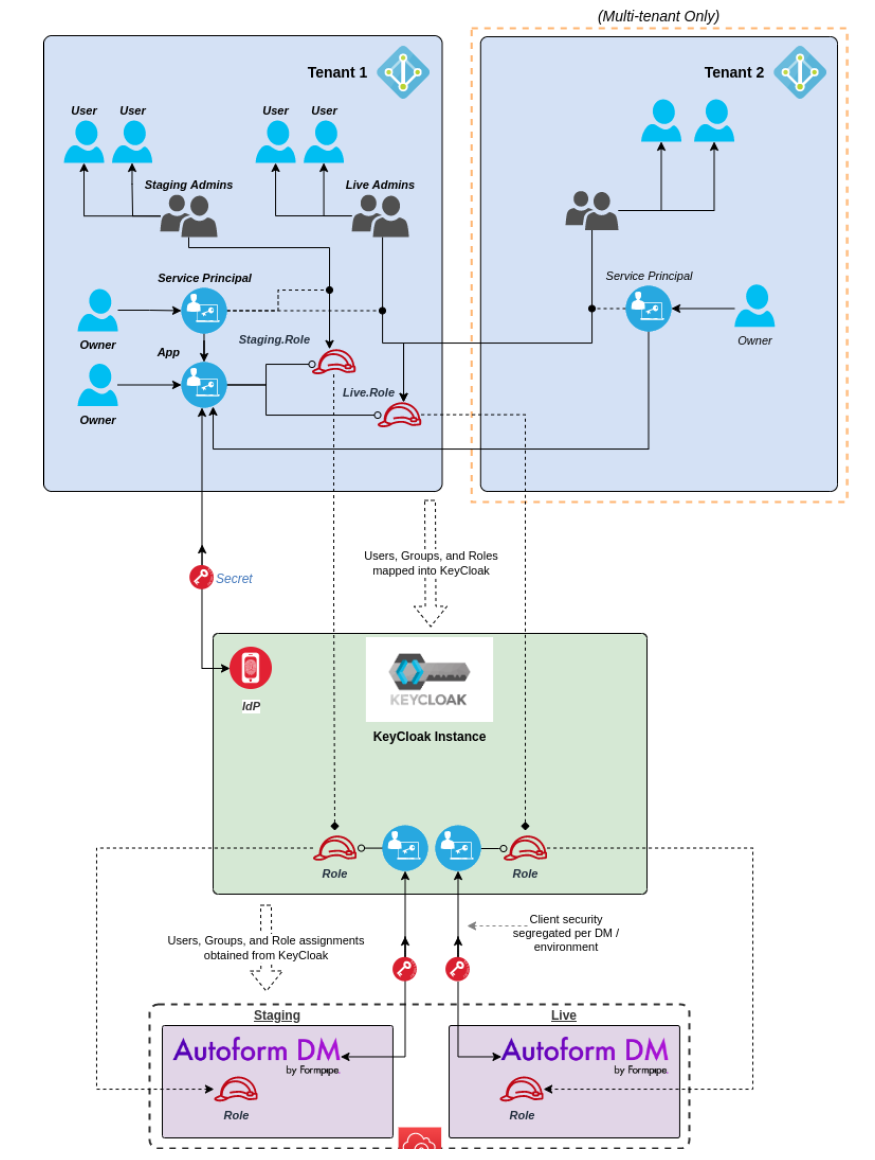
In this approach to security:
App roles are defined in the IdP app registration. Ultimately, each app role corresponds to a role on an Autoform DM environment.
Each app role’s name is prefixed to make it environment-specific.
In the IdP, users and groups are assigned app roles.
Keycloak roles that correspond to the Autoform DM environment-specific roles are created.
Each of the IdP app roles is mapped to the corresponding Keycloak role.
When Autoform DM receives information (from Keycloak) about a user’s role, it honors the role assignment made in Keycloak.
This enables role management to be centralized but comes with the cost of additional maintenance and configuration outside Keycloak.

